Categories Articles
Community Engagement is Mandatory for AI to Work in Under-Resourced Communities
Community Engagement and Needs Assessment: Example: Suppose we’re working with a low-income...
Harnessing AI for Under-Resourced Communities: Solutions and Implementation Strategies for Non-Profits
#3 Welcome back to the third installment of our blog series on the transformative potential of...
Implementing AI in Inner-City Communities: Detailed Insights and Strategies
#2 Implementing AI in Inner-City Communities: Detailed Insights and Strategies Introduction: As we...
Pros and Cons of Artificial Intelligence in Under-Resourced Communities
#1 Pros and Cons of Artificial Intelligence in Under-Resourced Communities Introduction Artificial...
VPNs Simple and Safe
A VPN, or virtual private network, creates a virtual “tunnel” of encrypted data running over the...
Why You Should Start Using A VPN
Why You Should Start Using a VPN September 28, 2019 | lmgtfy | VPNs And How to Choose the Best...
The Importance of Strong Passwords
Keep your computer, data and accounts safe with strong passwords. Your first line of defense on...
How To Create A Password You Can Remember
Five Methods:Using Phrases, Using Codes, Doubling It, The Bridge Shuffle, Upside-Down and...
KNC Jupiter Very First ASIC Bitcoin Miner
I am a Newbie to Crypto Currency. I'm also very lucky! Today, I had the good fortune to see one of...
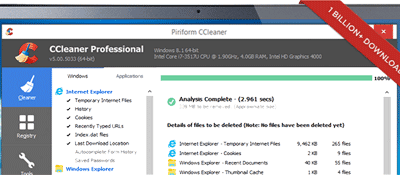
Keep Your Device Clean
Is your device running a bit slower than usual? Maybe random screens are popping up? Does your...
Tor Project
Another tool to consider for your anonymity and protection online, is the Tor Project. Below is...
Internet Security: College Bound!
As your son or daughter heads off to college, he or she is packing a smartphone, and undoubtedly...
Internet Security Tips For Students In Middle School And High School
Between the ages of 10 and 11 is, on average, when kids get their first cellphone. So by the time...
Internet Safety for Elementary School Students
With back-to-school preparations for clothing, backpacks and school supplies going on, keep in...
Common Mobile Phone Scams & How to Avoid Them
As smartphone technology continues to evolve, it also paves the way for an increasing amount of...
RACHEL PLUS CONTENT
Storyboard for RACHEL Plus Video-1 Today we’re going to look at some of what RACHEL is, connecting...
RACHEL-PLUS CONTENT-2
RACHEL-PLUS CONTENT-2 Storyboard for RACHEL Plus Content-2 1. RACHEL stands for Remote Access...
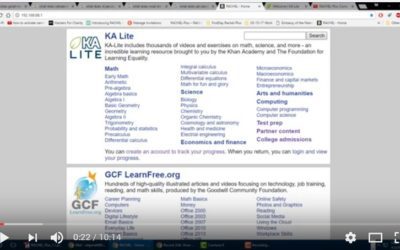
OffLine Education with RACHEL-Pi
Read More In the next few posts, I will share info about a learning tool I was introduced to. It...
Secure Your Passwords
Secure your passwords Passwords are the first line of defense against cyber criminals. It’s...
Prevent Identity Theft
Prevent Identity Theft Just like burglars and thieves, cyber criminals have many different ways to...
I Decided On A VPN
After several months of trying VPNs, I decided on IPVanish! It is fast! Some VPNs slow your...